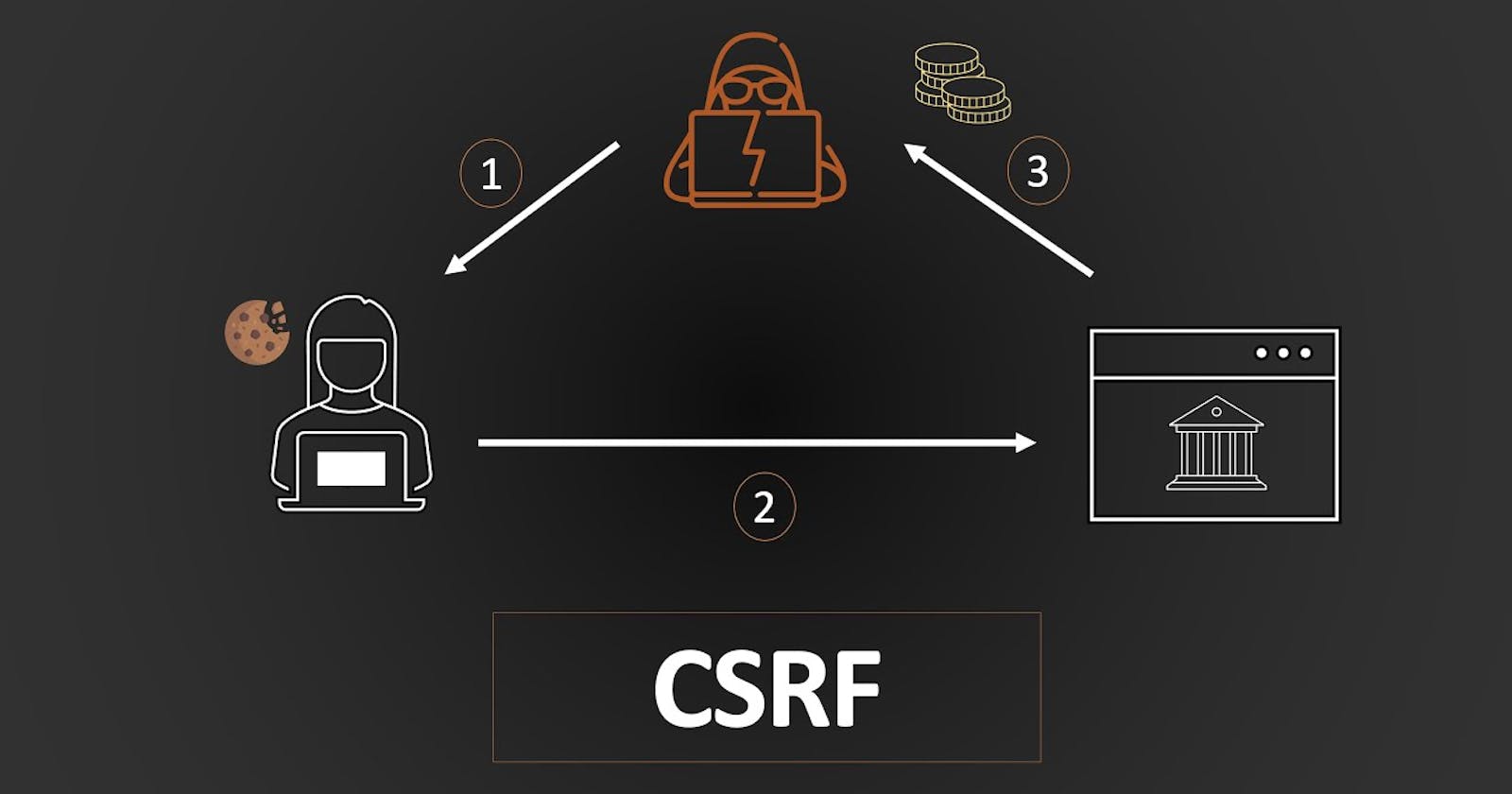
Hey there! Today, we're going to dive into the exciting world of CSRF (Cross-Site Request Forgery) tokens. They are like superheroes when it comes to protecting against CSRF attacks. But wait, what are they exactly? 🤔
Well, imagine a scenario where a malicious website tricks you into making a request on another website that you trust. Sneaky, right? This is a CSRF attack, and it can have some serious consequences. But fear not, because CSRF tokens are here to save the day!
CSRF tokens act as a shield against these attacks. They are unique, random, and securely generated tokens that are attached to every sensitive request made by a user. When a user interacts with a trusted website, the server generates a CSRF token and embeds it in the response it sends back to the user's browser.
Now, when the user performs an action that requires a sensitive request, like submitting a form, the CSRF token is included in the request. The server then checks if the token matches the one it generated earlier. If they match, hooray! The request is considered legitimate and is processed accordingly. 🎉 However, if the tokens don't match, the server knows something fishy is going on and the request is rejected. Nice save, right? 🛡️
But how should these CSRF tokens be generated? Let's find that out in this blog!
Topics to be covered:
Understanding CSRF Tokens
Best Practices for Generating CSRF Tokens
Secure Transmission of CSRF Tokens
Mitigating CSRF Vulnerabilities in Express and React
Extra Resources
Understanding CSRF Tokens: What Are They and Why Are They Important?
A CSRF Token is a secret, unique and unpredictable value a server-side application generates in order to protect CSRF-vulnerable resources.
A CSRF Token is an essential security measure used by server-side applications to safeguard vulnerable resources from cross-site request forgery attacks. It consists of a confidential, distinctive, and unpredictable value that is generated by the server-side application.
When a client makes a subsequent HTTP request, the server-side application generates and includes the CSRF token in the request. This token is then compared with the token stored in the user session. If the token is absent or doesn't match the value in the user session, the request is denied, the user session is terminated, and the event is logged as a potential CSRF attack.
Best Practices for Generating CSRF Tokens
CSRF tokens, like session tokens, need to possess substantial randomness and strong unpredictability to guarantee security.
To achieve this, a reliable pseudo-random number generator (PRNG) with cryptographic strength can be utilized. The PRNG should be seeded with a combination of the creation timestamp and a static secret.
For enhanced security, individual tokens can be generated by incorporating user-specific entropy into the chaining process. Afterwards, the entire structure can be securely hashed.
By following these practices, malicious users attempting to analyze tokens based on samples provided to them face additional obstacles.
To summarize, here are the key principles for token generation and verification:
Utilize a reputable random number generator that offers sufficient entropy.
Prevent token reuse by setting an expiration time for tokens.
Safely verify that the received token matches the set token. One approach is to compare hashes.
Avoid transmitting CSRF tokens via HTTP GET requests. This prevents direct exposure of the token in the URL and avoids leakage through the Referer header along with other referrer information.
For Example, A CSRF token in Express can be generated as follows:
const express = require('express');
const crypto = require('crypto');
const app = express();
// Middleware to generate and attach the CSRF token to the requests
app.use((req, res, next) => {
const csrfToken = crypto.randomBytes(32).toString('hex');
req.csrfToken = csrfToken;
res.cookie('csrfToken', csrfToken, { httpOnly: true, secure: true, sameSite: 'lax' });
next();
});
// Example route handling CSRF-protected form submission
app.post('/submit', (req, res) => {
const { csrfToken } = req.body;
if (csrfToken === req.csrfToken) {
// Token is valid
res.send('Form submission successful!');
} else {
// Token is invalid
res.status(403).send('Invalid CSRF token');
}
});
app.listen(3000, () => {
console.log('Server started on port 3000');
});
When you verify, compare the hashes. If both the token and the form are valid, the hashes will match.
Secure Transmission of CSRF Tokens: Guidelines and Recommendations
CSRF tokens are crucial secrets and must be handled securely throughout their lifecycle.
To transmit the token to the client, consider using a hidden HTML form field with the POST method. By including the token as a request parameter when the form is submitted, you can enhance security. Remember to place the CSRF token field early in the HTML file, before any non-hidden fields or user-controllable data, to minimize the risk of attacks that manipulate the HTML document.

For example:
<form action="/transfer.do" method="post">
<input type="hidden" name="CSRFToken" value="OWY4NmQwODE4ODRjN2Q2NTlhMmZlYWEwYzU1YWQwMTVhM2JmNGYxYjJiMGI4MjJjZDE1ZDZMGYwMGEwOA==">
[...]
</form>
While placing the CSRF token in the URL query string is possible, it is less secure because the query string can be logged, transmitted to third parties within the HTTP Referer header, or displayed on-screen within the user's browser.
To further protect against token prediction or capture, you can insert the CSRF token in a custom HTTP request header using JavaScript. This approach is well-suited for AJAX or API endpoints. However, note that sending custom headers cross-domain may be restricted by browsers. It's important to consider the complexity of this approach for your specific situation, as it may not be necessary in many cases.
Remember, never transmit CSRF tokens within cookies as it can introduce additional security risks.
It's essential to regularly review and update CSRF token implementation based on the latest security best practices.
Mitigating CSRF Vulnerabilities in Express and React
CSRF protection in Express:
Express is a backend web framework for Node.js. It is fast, flexible and minimalistic. It’s free and open source.
Since Express is a minimalistic web framework, it doesn’t support any anti-CSRF measures by default. But it provides a pluggable middleware that helps your web server to protect itself against CSRF attacks.
The middleware is known as “csurf”, and it’s super easy to set up in your project. It offers some bootstrap options as well to configure its functionality.
CSRF protection in React
React is a front-end framework developed by Facebook. It’s free and open source and is mostly used for building mobile or single-page applications.
Unlike Angular, React doesn’t come with a default security measure against CSRF attacks.
In order to protect a React application against CSRF, you have to introduce a security solution in your app, and have the web server support it.
Luckily, it’s easy to implement CSRF protection in React. You only have to store the CSRF token in your React app and generate relevant headers to send along with the request to the server. The server will quarantine all CSRF requests.
Want to learn more about CSRF?
Have a look at these articles:
Conclusion
In conclusion, CSRF tokens play a vital role in safeguarding web applications against cross-site request forgery attacks. By treating these tokens as secrets and managing them securely throughout their lifecycle, developers can significantly enhance the security of their applications. Transmitting CSRF tokens within hidden HTML form fields using the POST method is a recommended approach, ensuring that the token is included as a request parameter when forms are submitted. Placing the CSRF token early in the HTML file, before user-controllable data, mitigates potential attacks that manipulate the document. It is crucial to avoid transmitting CSRF tokens in the URL query string or within cookies, as these methods pose additional security risks. As web technologies evolve, staying informed about the latest best practices and regularly reviewing and updating CSRF token implementation is paramount to maintaining a strong defense against potential threats. By prioritizing the protection of CSRF tokens, developers can bolster the security of their applications and provide a safer user experience for their users.